A Guide to Understanding Blockchain Consensus Algorithms
Blockchain is a distributed, decentralized network that provides greater immutability, security, and transparency. We certainly understand that!
However, have you ever questioned how it manages to accomplish all of this?
If there is no central authority, who controls this network and oversees each transaction?
Sounds fascinating, yes?
In this comprehensive instructional material, we will focus on Blockchain consensus algorithms, which are at the very heart of the world of Blockchain development.
What is Blockchain Consensus Algorithm?
Coming to a single data value, achieving overall system reliability and making decisions in the midst of distributed processes and decentralized network systems are accomplished by a function in computer science, called Consensus Algorithm. The agreement mechanism has been developed so that the processes of the systems agree on the data value and concur with the idea of how that should get utilized in multi-agent systems or distributed computing. The function has been most commonly deployed in Blockchain today. Blockchain, a decentralized technology as such, needed to find out a way to make decisions without meddling with its security and this is where Consensus Algorithm kicked in.
Purpose of Blockchain Consensus Algorithm
Unified Agreement:
The consensus Algorithm makes it convenient, shields and protects from interferences while reaching an agreement on the state and activities of the network. Achieving this is one of the prime objectives of the Consensus Algorithm. The embedded protocols of the blockchain make sure that the data involved are accurate, true and in contrast to centralized systems, trust in any single agent or authority is not required.
Reliability:
Another crucial utilization of the Consensus Algorithm is that it ensures that the blockchain while being fault tolerant, maintains its consistency and reliability. It also helps in fending off menaces of cyber-attacks and malware etc.
Fair and equitable:
Consensus Algorithms permit anyone to join and participate in the network. This way, the process aligns with the open-source feature and the decentralization characteristic of blockchain.
No double-spending:
Fraudulent behavior such as double-spending, which means using a digital currency twice, is prevented. This responsibility of making sure that the currency is spent only once lies with the Consensus Algorithm.
Scalability and Performance:
The consensus Algorithm can take care of a large number of transactions while achieving great performance and speed. As the transactions increase in number, the algorithm handles the extra load without jeopardizing either performance or security.
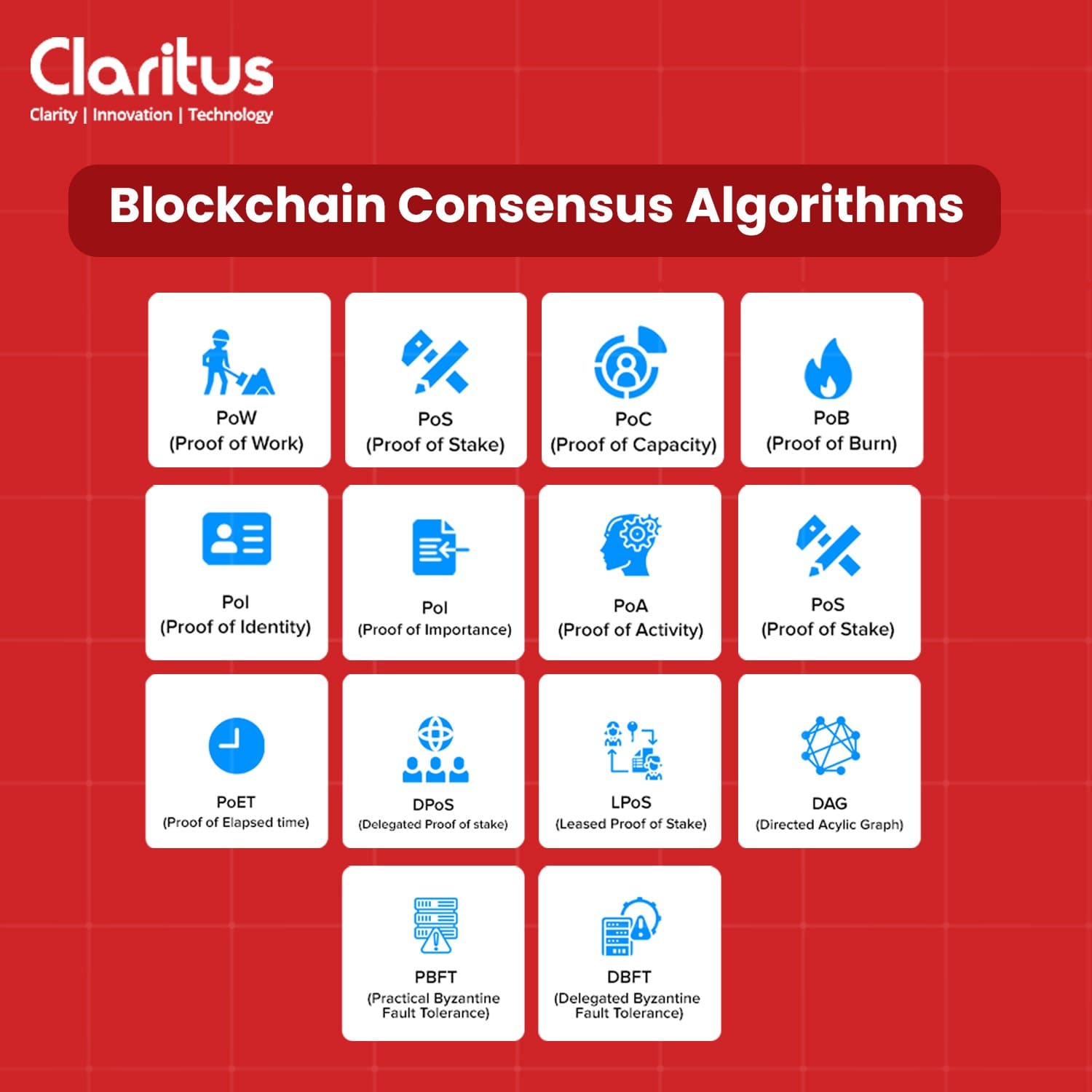
Popular Blockchain Consensus Algorithms in Market
1. Proof of Work (PoW)
This original consensus algorithm is utilized by Bitcoin as well as various other cryptocurrencies. PoW is highly secure. Users and miners need to perform a significant amount of complex mathematical calculations and computational work for validating transactions, adding fresh blocks to the chain, and achieving consensus. Newly minted coins are gifted to the first miner who finds a solution. However, PoW is rather slow and also known for its energy-intensive computational work which restricts its ability to process a significantly high number of transactions.
2. Proof of Stake (PoS)
PoS is more energy efficient than PoW. In order to validate transactions, users are selected on account of the amount of cryptocurrency they possess or the stakes they hold. These validators then oversee the validation of transactions and the addition of new blocks to the chain. This system apparently reduces the decentralization characteristic of the network to a certain extent. However, rewards are available with respect to a validator’s stake. Additionally, although known for its speed and effectiveness, PoS is also regarded as less secure than PoW.
-
Delegated Proof of Stake (DPoS)
This one is a variation of PoS, which uses a smaller set of elected validators for validating transactions. Elected by coin holders, these validators are in charge of inserting new blocks into the chain. Users need to comply with certain eligibility criteria to become validators and they are rewarded with freshly minted coins. DPoS is notable for its energy efficiency, scalability and swift processing of transactions. Notwithstanding this, with only a small group of validators, it’s regarded and condemned as more centralized than other Consensus Algorithms.
-
Leased Proof of Stake (LPoS)
LPoS, This is another variation of PoS, is a consensus mechanism employed within the delegated proof of stake (DPoS) systems to overcome the limitations encountered in traditional proof of stake (PoS) algorithms. Within an LPoS framework, individuals who possess tokens have the option to lease them to a trustworthy validator, thereby augmenting their stake and improving their chances of being chosen as block producers. This leasing process heightens the likelihood of the validator creating blocks, while the token holders receive a share of the validator’s block rewards as compensation.
LPoS presents various advantages when compared to conventional PoS systems, including benefits such as enhanced liquidity, flexibility, and security. It’s important to note that LPoS is specific to particular blockchain platforms that implement delegated proof of stake, and the specific implementation and details can vary depending on the associated blockchain protocol and its governing rules.
3. Proof of Authority (PoA)
PoA is a modified version of PoS which consists of a set of pre-approved validators whose identities are known and thus offer a very high level of security. The identities are verified with the personal identifications and official documentation of the validators. Therefore, they put their reputations and identities at stake and risk while being the only ones permitted to add new blocks. Incentives are provided to these stakeholders for securing and preserving the blockchain network. Here, the number of validators is quite small, many a time around 25 and that makes PoA less decentralized than PoW or PoS.
4. Byzantine Fault Tolerance (BFT)
Byzantine Fault Tolerance (BFT) is a critical characteristic of distributed systems, especially within blockchain and consensus algorithms. It denotes the capability of a system to sustain proper functionality and achieve consensus even in the presence of malicious nodes or faults. BFT protocols address these complexities by providing a robust mechanism to withstand Byzantine faults. Algorithms such as Practical Byzantine Fault Tolerance (PBFT), Tendermint, and Byzantine Fault Tolerant State Machine Replication (BFT-SMR) have been developed to uphold the system’s integrity, security, and availability when confronted with faulty or malicious nodes.
BFT holds particular significance in decentralized systems like blockchain, wherein networks comprise numerous nodes exhibiting varying levels of trustworthiness. By accommodating Byzantine faults, BFT consensus algorithms enhance the resilience and dependability of the distributed system, bolstering its resistance against attacks and ensuring the consistency of the shared ledger or state.
-
Practical Byzantine Fault Tolerance (PBFT)
PBFT is a lightweight Consensus Algorithm, usually deployed in permissioned blockchain networks. It resolves the Byzantine Generals’ Problem by permitting users to confirm their delivered messages and computing for evaluation of the credibility and legitimacy of those messages. There’s a complex voting process involved and the decision is shared with other nodes that eventually arrive at a consensus over it. PBFT is also recognized for its swiftness and efficiency but needs a dependable set of validators. It’s also apparently less secure in open networks.
-
Delegated Byzantine Fault Tolerance (DBFT)
Delegated Byzantine Fault Tolerance (DBFT) is a consensus algorithm that combines the concepts of Byzantine fault tolerance and delegation. It involves a set of trusted validators, known as delegates or block producers, who validate transactions, create new blocks, and ensure the integrity of the blockchain. The DBFT algorithm proceeds through several rounds of block production and validation, with a single delegate as the primary validator and other delegates as backup validators. The primary validator proposes a block, and the other delegates participate in a voting process to approve or reject the block. If the majority of delegates agree on its legitimacy, the block is added to the blockchain.
DBFT ensures Byzantine fault tolerance by requiring a threshold of honest and trusted delegates to reach consensus. Some blockchain platforms, like NEO and Ontology, employ DBFT to achieve fast block confirmation times, high transaction throughput, and robust Byzantine fault tolerance.
5. Proof of Importance (PoI)
PoI is a consensus algorithm almost similar to PoS. A node’s importance score is evaluated for its chances of being employed for the creation of a new block. The importance score is found out with respect to a node’s gross performance, encompassing the number of transactions it handled and the number of nodes it could refer to the network. New Economy Movement (NEM) blockchain uses PoI where a special harvesting system is used for nodes to earn transaction fees.
6. A Direct Acyclic Graph (DAG)
A Direct Acyclic Graph (DAG) is a data structure where nodes are connected by directed edges, forming a graph without any cycles. DAGs find applications in computer science, mathematics, scheduling, and blockchain technology to represent dependencies or relationships. In the realm of blockchain, DAG-based blockchains, commonly referred to as “DAG ledgers,” utilize a DAG structure to organize and validate transactions. This approach enables a more flexible and efficient transaction validation process compared to traditional blockchain architectures.
DAG-based blockchains exhibit higher scalability and transaction throughput by allowing concurrent and asynchronous processing within the graph. Moreover, these blockchains often employ a consensus mechanism known as “weighted voting” or “weighted influence” to eliminate the need for resource-intensive mining, resulting in enhanced energy efficiency. Notable examples of DAG-based blockchain projects include IOTA and Nano, both offering scalable and feeless transaction capabilities.
7. Proof of Capacity (PoC)
Proof of Capacity (PoC) is a consensus mechanism in blockchain networks that validates and safeguards transactions, offering an alternative to traditional proof-of-work (PoW) or proof-of-stake (PoS) algorithms. PoC involves miners allocating storage space on their devices to find a solution to a cryptographic puzzle. Once a valid solution is found, miners can create new blocks and append them to the blockchain, earning block rewards. PoC offers energy efficiency, decentralization, and resistance to specialized mining hardware like ASICs, preventing the centralization of mining power. Examples of blockchain projects using PoC include Burstcoin and Chia Network.
8. Proof of Burn (PoB)
Proof of Burn (PoB) is a consensus mechanism utilized in blockchain networks, enabling participants to exhibit their dedication by permanently obliterating a specific quantity of cryptocurrency or tokens. This act of burning tokens functions as proof of the expended economic value and permits participants to engage in the validation and consensus processes of blocks. The likelihood of being chosen as a validator or block producer within PoB systems typically corresponds to the volume of tokens burned.
The fundamental objective of PoB is to align the interests of network participants and ensure their vested interest in the triumph of the network. PoB brings forth advantages such as energy efficiency, discourages the concentration of power, and fosters incentives for active network involvement. Slimcoin and Counterparty are noteworthy blockchain projects that have implemented the PoB consensus mechanism.
9. Proof of Identity (PoI)
Proof of Identity (PoI) holds significant importance within blockchain networks and digital systems as it guarantees the genuineness and reliability of participants’ identities. It necessitates the provision of evidence or credentials to validate one’s identity, thus fortifying security measures, deterring fraudulent activities, and fostering trust among network participants. PoI systems typically encompass a combination of automated checks and manual verification conducted by trusted entities or authorities.
The ultimate objective of PoI is to establish a secure and trustworthy environment that facilitates secure interactions and transactions among users. The implementation of PoI varies depending on the specific blockchain protocol or digital system in use, and its implications stretch beyond blockchain applications to encompass online platforms encompassing financial systems, social media platforms, and e-commerce platforms.
10. Proof of Activity (PoA)
Proof of Activity (PoA) represents a hybrid consensus mechanism that merges elements from both proof-of-work (PoW) and proof-of-stake (PoS) algorithms to safeguard blockchain networks. Its objective is to strike a balance between energy efficiency and security by mandating participants to engage in computational work during the mining phase and stake their tokens for transaction validation.
The initial PoW mining stage guarantees network security during early developmental phases, while the subsequent PoS validation phase introduces efficiency and economic benefits. This combination capitalizes on the security advantages of PoW while curbing energy consumption. Participants with larger stakes enjoy higher chances of being selected as validators, promoting their inclination to hold and invest in the network’s native cryptocurrency or tokens.
PoA facilitates enhanced energy efficiency in contrast to pure PoW algorithms and heightens network security by necessitating a blend of computational work and stake ownership. Noteworthy blockchain projects that have implemented PoA include Decred and Komodo.
11. Proof of Elapsed Time (PoET)
Proof of Elapsed Time (PoET) is a consensus mechanism employed in blockchain networks to achieve distributed consensus while avoiding the need for computationally intensive calculations seen in traditional Proof of Work (PoW) algorithms. PoET utilizes a trusted execution environment (TEE) and randomization to establish the order of block creation, assigning the privilege to the validator with the shortest waiting time. This approach guarantees fairness and thwarts validators from predicting the outcome.
By diminishing resource requirements, PoET fosters energy efficiency and scalability within blockchain networks. The TEE plays a critical role by securely generating waiting times, preventing dishonest practices, and ensuring impartial determination. Prominent blockchain projects such as Hyperledger Sawtooth have implemented PoET to address concerns related to scalability and energy efficiency, thereby contributing to the development of a sustainable and environmentally conscious blockchain ecosystem.
Conclusion
Just like the Blockchain Consensus Algorithms mentioned above, with the passage of time countless others will be designed for maximum utilization of available resources to reach an agreement and to secure the network as well. It’s important to note, however, that a mix of two consensus algorithms can also be used in a network to accomplish the desired outcome.